CoinGecko Bug Bounty Program


CoinGecko provides a fundamental analysis of the crypto market. In addition to tracking price, volume and market capitalization, CoinGecko tracks community growth, open-source code development, major events and on-chain metrics.


BOUNTY CAMPAIGN
CoinGecko Bug Bounty Program
Activity type:
/
Bug Bounty
Dates:
22 Jul 2020
-
TBA
Registration:
OPEN
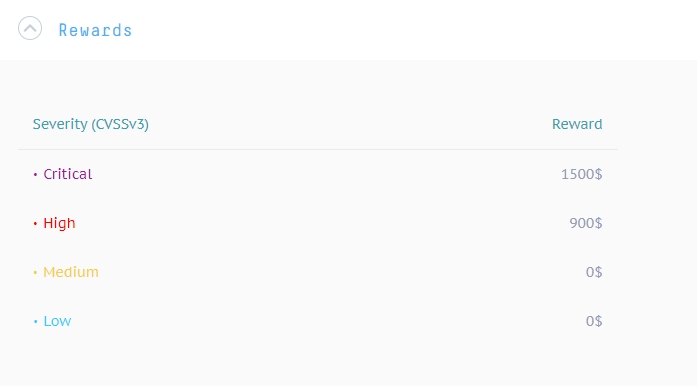
Personal reward:
$900+
(Not set)
Difficulty:
HARD
Links:
Ends in:
Focus Area
IN-SCOPE VULNERABILITIES
We are interested in the following vulnerabilities:
OUT-OF-SCOPE VULNERABILITIES
OUT OF SCOPE - WEB
Vulnerabilities found in out of scope resources are unlikely to be rewarded unless they present a serious business risk (at our sole discretion). In general, the following vulnerabilities do not correspond to the severity threshold:
OUT OF SCOPE - MOBILE
We are interested in the following vulnerabilities:
- Business logic issues
- Remote code execution (RCE)
- Database vulnerability, SQLi
- File inclusions (Local & Remote)
- Access Control Issues (IDOR, Privilege Escalation, etc)
- Leakage of sensitive information
- Server-Side Request Forgery (SSRF)
- Other vulnerability with a clear potential loss

| Target | Type | Severity | Reward |
|---|---|---|---|
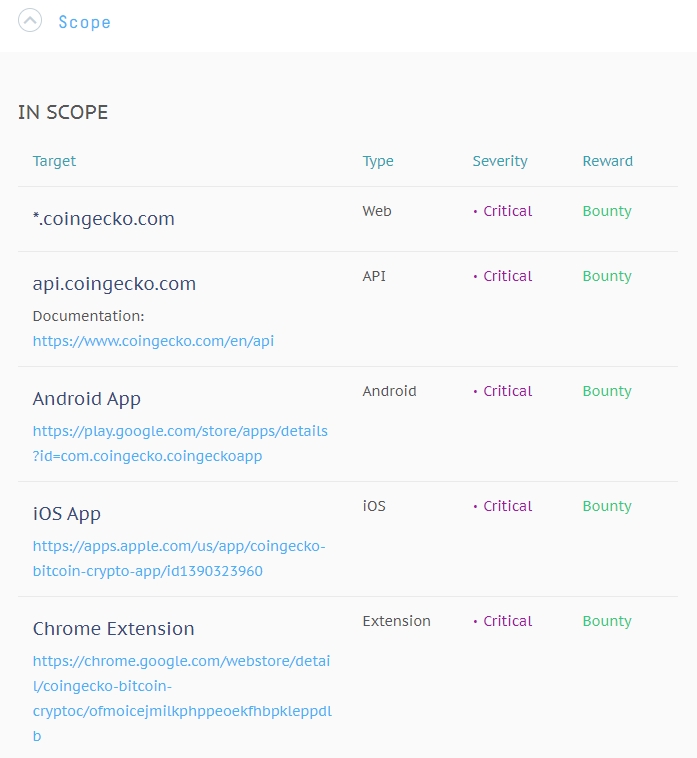
*.coingecko.com | Web | Critical | Bounty |
api.coingecko.comDocumentation: https://www.coingecko.com/en/api | API | Critical | Bounty |
Android Apphttps://play.google.com/store/apps/details?id=com.coingecko.coingeckoapp | Android | Critical | Bounty |
iOS Apphttps://apps.apple.com/us/app/coingecko-bitcoin-crypto-app/id1390323960 | iOS | Critical | Bounty |
Chrome Extensionhttps://chrome.google.com/webstore/detail/coingecko-bitcoin-cryptoc/ofmoicejmilkphppeoekfhbpkleppdlb | Extension | Critical | Bounty |
OUT-OF-SCOPE VULNERABILITIES
OUT OF SCOPE - WEB
Vulnerabilities found in out of scope resources are unlikely to be rewarded unless they present a serious business risk (at our sole discretion). In general, the following vulnerabilities do not correspond to the severity threshold:
- Vulnerabilities in third-party applications
- Best practices concerns
- Recently (less than 30 days) disclosed 0day vulnerabilities
- Vulnerabilities affecting users of outdated browsers or platforms
- Social engineering, phishing, physical, or other fraud activities
- Publicly accessible login panels without proof of exploitation
- Reports that state that software is out of date/vulnerable without a proof of concept
- Vulnerabilities involving active content such as web browser add-ons
- Most brute-forcing issues without clear impact
- Denial of service
- Theoretical issues
- Moderately Sensitive Information Disclosure
- Spam (sms, email, etc)
- Missing HTTP security headers
- Infrastructure vulnerabilities, including:
- Certificates/TLS/SSL related issues
- DNS issues (i.e. MX records, SPF records, etc.)
- Server configuration issues (i.e., open ports, TLS, etc.)
- Open redirects
- Session fixation
- User account enumeration
- Clickjacking/Tapjacking and issues only exploitable through clickjacking/tap jacking
- Descriptive error messages (e.g. Stack Traces, application or server errors)
- Self-XSS that cannot be used to exploit other users
- Login & Logout CSRF
- Weak Captcha/Captcha Bypass
- Lack of Secure and HTTPOnly cookie flags
- Username/email enumeration via Login/Forgot Password Page error messages
- CSRF in forms that are available to anonymous users (e.g. the contact form)
- OPTIONS/TRACE HTTP method enabled
- Host header issues without proof-of-concept demonstrating the vulnerability
- Content spoofing and text injection issues without showing an attack vector/without being able to modify HTML/CSS
- Content Spoofing without embedded links/HTML
- Reflected File Download (RFD)
- Mixed HTTP Content
- HTTPS Mixed Content Scripts
- DoS/DDoS issues

| Target | Type | Severity | Reward |
|---|---|---|---|
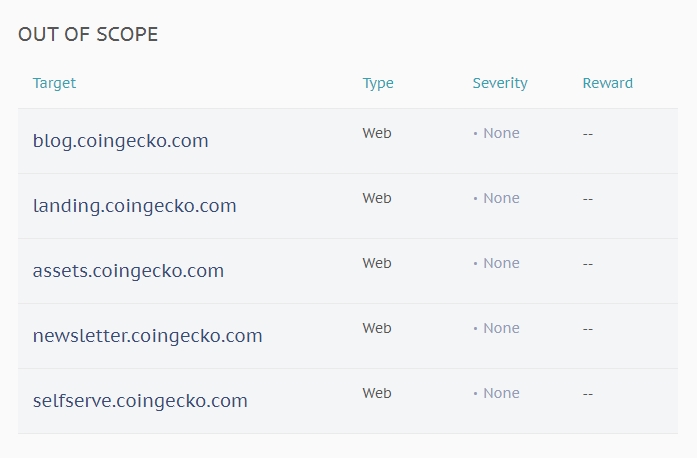
blog.coingecko.com | Web | None | -- |
landing.coingecko.com | Web | None | -- |
assets.coingecko.com | Web | None | -- |
newsletter.coingecko.com | Web | None | -- |
selfserve.coingecko.com | Web | None | -- |
OUT OF SCOPE - MOBILE
- Attacks requiring physical access to a user's device
- Vulnerabilities requiring extensive user interaction
- Exposure of non-sensitive data on the device
- Reports from static analysis of the binary without PoC that impacts business logic
- Lack of obfuscation/binary protection/root(jailbreak) detection
- Bypass certificate pinning on rooted devices
- Lack of Exploit mitigations i.e., PIE, ARC, or Stack Canaries
- Sensitive data in URLs/request bodies when protected by TLS
- Path disclosure in the binary
- OAuth & app secret hard-coded/recoverable in IPA, APK
- Sensitive information retained as plaintext in the device’s memory
- Crashes due to malformed URL Schemes or Intents sent to exported Activity/Service/Broadcast Receiver (exploiting these for sensitive data leakage is commonly in scope)
- Any kind of sensitive data stored in app private directory
- Runtime hacking exploits using tools like but not limited to Frida/ Appmon (exploits only possible in a jailbroken environment)
- Shared links leaked through the system clipboard
- Any URIs leaked because a malicious app has permission to view URIs opened.
- Exposure of API keys with no security impact (Google Maps API keys etc.)
- Avoid using web application scanners for automatic vulnerability searching which generates massive traffic
- Make every effort not to damage or restrict the availability of products, services or infrastructure
- Avoid compromising any personal data, interruption or degradation of any service
- Don’t access or modify other user data, localize all tests to your accounts
- Perform testing only within the scope
- Don’t exploit any DoS/DDoS vulnerabilities, social engineering attacks or spam
- Don’t spam forms or account creation flows using automated scanners
- In case you find chain vulnerabilities we’ll pay only for vulnerability with the highest severity.
- Don’t break any law and stay in the defined scope
- Any details of found vulnerabilities must not be communicated to anyone who is not a HackenProof Team or an authorized employee of this Company without appropriate permission

Links:

COMMENTS